This guide provides communications directors, PR managers, and crisis teams with a comprehensive 5-step response plan for deepfake incidents targeting executives. It covers rapid detection using social listening, immediate containment strategies calibrated to threat level, audience-segmented communications, implementation of AI-powered detection technology, and long-term prevention through simulated drills and authentication protocols. With deepfake incidents increasing by 1,740% and costing companies millions, this actionable framework enables organizations to quickly identify, contain, and mitigate deepfake threats while establishing robust prevention systems.
The Deepfake Threat to Corporate Reputation
Deepfakes pose an insidious threat to corporate reputation. Engineering firm Arup lost $25 million after fraudsters orchestrated a deepfake video call impersonating executives. North America experienced a 1,740% increase in deepfake fraud in 2023 according to Eftsure. With deepfake content projected to increase from 500,000 instances in 2023 to 8 million by 2025 (TechRadar), organizations need a clear action plan. What makes deepfakes particularly dangerous is their ability to spread virally before companies can respond.
This guide provides a five-step response plan for when your brand becomes targets of deepfake attacks.
STEP 1: Rapid Detection and Verification
Implement 24/7 Social Listening
You may already have social listening tools running. If they aren’t already, they should also be set-up to flag unusual activities:
- Sudden velocity increases in mentions of the brand or executives
- Unusual platform distribution of content
- Out-of-character statements attributed to leadership or the brand
- Clustering of suspicious content from multiple sources
Establish Verification Processes
Before jumping in, first confirm what it is you are dealing with.
Conduct digital forensic analysis to identify manipulation indicators. Deepfakes are becoming harder to spot to the human eye and detection tools should help reduce the guesswork. While checking the content itself, assess the credibility of the source and whether the account looks real or fake.
Document all verification steps for response messaging and potential legal actions. A verification audit trail strengthens your position when countering false narratives.
Activate Your Team…Preferably in Minutes
Organizations could have just minutes from detection to activate response before content gains significant traction. Time is of the essence. This requires:
- Create your response team with clear roles
- Pre-approved response templates
- Establish notification systems with escalation protocols
STEP 2: Immediate Containment and Control
First-Hour Containment Checklist
The first 60 minutes are critical for containment. Implement tiered response based on exposure level:
Low Exposure (<10,000 views)
- Submit platform takedown requests
- Deploy digital fingerprinting to track variations
- Notify key stakeholders with holding statements
Medium Exposure (10,000-100,000 views)
- Activate monitoring to identify spread patterns
- Identity the accounts sharing the deepfake and assess the balance between fake vs real amplification.
- Prepare to brief internal stakeholders, and possibly external audiences such as journalists, using the evidence you have gathered so far
High Exposure (>100,000 views)
- Implement full crisis communications
- Distribute multimedia evidence of falsification
- Confirm the veracity of the accounts involved in the conversation using third-party verification services
- Mobilize relevant legal teams and consider emergency legal injunctions
Case Study: Successful Containment
WPP Case Study: When facing a CEO deepfake announcing a fictional merger, they implemented immediate platform reporting through partner channels, direct outreach to financial media, and deployed a video statement from the real CEO within 45 minutes.
Ferrari Case Study: When confronted with a deepfake showing their CEO making false claims, they flagged content as false through verified accounts, published timestamped evidence of the CEO’s actual location, and engaged their customer community to help report content.
Effective containment creates space for your strategic communications response.
STEP 3: Strategic Communications Response
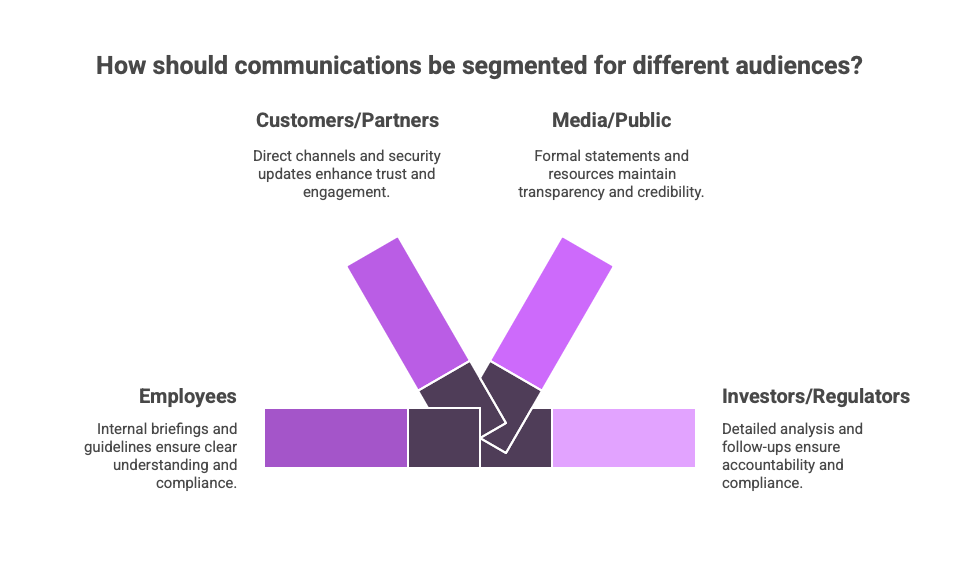
Deploy Audience-Segmented Messaging
For Employees: Internal briefings, response guidelines, authentication evidence, and FAQ documents.
For Customers/Partners: Direct communications with verification points, dedicated contact channels, and security measure updates.
For Media/Public: Formal statements with technical details, visual comparison materials, expert availability, and fact-checking resources.
For Investors/Regulators: Formal notifications with detailed analysis, remediation steps, risk assessments, and scheduled follow-ups.
STEP 4: Implement Advanced Detection Technology
Utilize AI-Powered Detection
Cyabra has developed technology to identify subtle manipulation markers:
- Facial inconsistencies and unnatural movements
- Audio/visual synchronization discrepancies
- Lighting and shadow inconsistencies
- Metadata anomalies indicating manipulation
Advanced detection represents an investment, but with deepfake fraud causing over $200 million in quarterly losses Security Magazine, the cost is minimal compared to potential damage from undetected deepfakes.
Integrate with Existing Monitoring
Connect detection systems with your monitoring infrastructure:
- Link to social listening platforms
- Integrate with media monitoring services
- Establish automated alerts for suspicious content
- Create verification workflows for detected threats
Organizations with integrated detection identified threats 4.3 hours faster than those using siloed approaches (International Compliance Association).
STEP 5: Long-term Reputation Recovery and Prevention
Conduct Simulated Drills
Implement deepfake simulations, ideally every quarter, to test response capabilities:
- Simulate realistic scenarios targeting your brand and executives
- Test team response times
- Evaluate containment effectiveness
- Identify verification process gaps
Establish Authentication Protocols
Implement comprehensive authentication for executive communications:
- Digital signatures for authentic content
- Consistent delivery channels for important announcements
- Executive communication style guides to identify anomalies
- Implement Cyabra’s proactive monitoring
CONCLUSION: Staying Ahead of the Threat
Organizations that proactively update response plans quarterly are 3.7 times more likely to effectively contain deepfake incidents than those with static approaches. With deepfake content projected to increase 16-fold by 2025, continuous adaptation is essential.
Rather than viewing a deepfake incident as a crisis, transform it into an opportunity to demonstrate leadership in digital integrity. The ability to quickly identify, contain, and counteract deepfakes can be a competitive advantage protecting your most valuable asset: your reputation.
_____________
Cyabra’s platform delivers advanced AI-powered detection, multi-signal monitoring, and real-time alerting. Cyabra specializes in detecting inauthentic behavior using AI to identify fake accounts, coordination patterns, and misinformation campaigns, transforming crisis management from reactive damage control to proactive reputation defense. Contact us to learn more.