Boycott Similac
Authenticity analysis of the profiles spreading negative Twitter conversation on Similac.
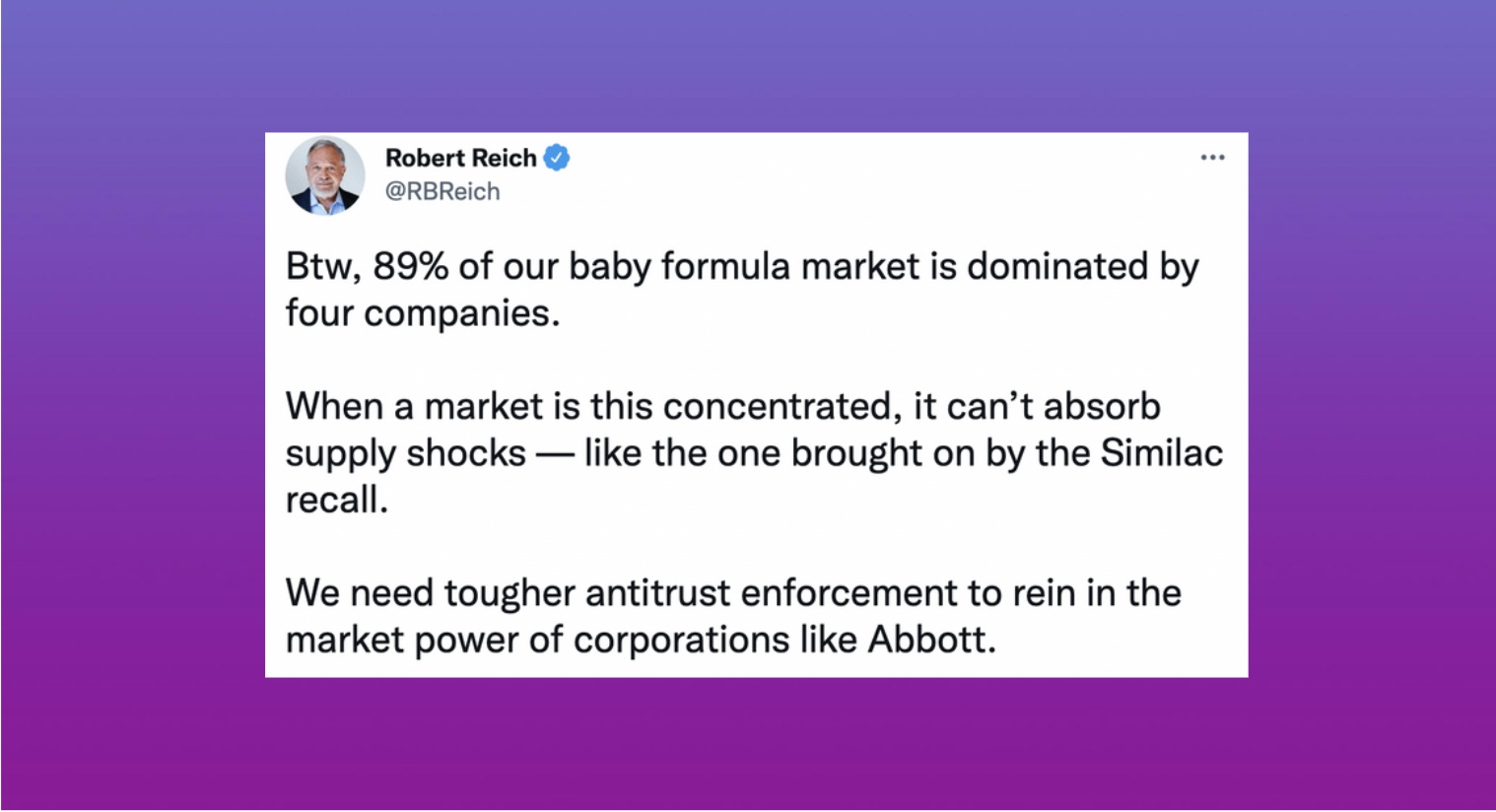
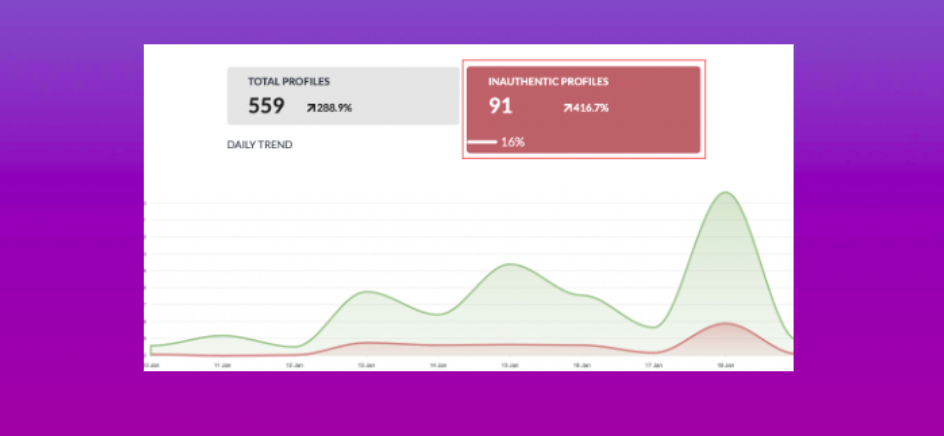
Analysis of over 20,000 Twitter accounts who commented on Similac and Abbott found that just over 5% of comments were from inauthentic users. However, in total, nearly a quarter of comments were negative, with much of the negative commentary coming from authentic users, many of whom regularly comment on parenting matters. Two inauthentic users who drove negative commentary were heavily tied into a community of inauthentic accounts.
#National Security
Fill up the form below and receive the full report directly to your inbox
Related reports
Pizza Hut – Social Media Analysis
June 10, 2024
Cyabra analyzed the primary factors contributing to the online boycott of Pizza Hut on X and Facebook.
Boycott Woolworths – Fake Activity Analysis
June 12, 2024
Cyabra identified the involvement of fake accounts surrounding the boycott of Woolworths.
Climate Crisis Misinformation Report
January 2, 2022
An analysis of climate change misinformation spread by real and fake profiles.