Personal reputation is now frontline in the information war. Attacks on executives, celebrities, and high-profile individuals have spiked – fast, personal, and often coordinated. In a matter of minutes, a false narrative can spread.
This playbook, based on Cyabra’s live event, “The Digital Bodyguard: Protecting Personal Reputations From Disinformation” shares practical, actionable guidance on how to defend yourself and your organization, by leading experts Simon Paterson MBE, Co-Founder of InfauxTech & Former US Head of Counter Disinformation at Edelman, and Pavel Trosin, Head of Monitoring and Insights at Schillings.
This guide will cover:
- The rise of personal disinformation attacks
- Why emotion drives virality and loss of control
- Spotting and assessing threats before they escalate
- The role of intent, context, and speed in response
- The 5D framework for rapid defense
- Building cross-functional trust ops
- From crisis response to lasting resilience
Why personal reputations are uniquely vulnerable
Today’s attacks are faster, more personal, and more varied than ever. Simon Patterson notes that targeting individuals produces an emotional reaction that amplifies impact: “It is that specific very pointed target that feels very personal that actually ratches it up that anxiety.”
There are three drivers behind the recent surge in personal-targeted disinformation.
- Technology: AI and cheap tools make deepfakes, cloned voices, fake profiles, and automated campaigns easy to produce at scale. Language models make convincing false content cheap and fast. Pave warns that tools to create false content have “absolutely exploded at an unprecedented kind of pace and scale.”
- Emotion: One single tweet can literally rewrite the whole narrative about who you are, and attacks on people generate stronger emotional responses than attacks on brands.
- Societal shifts: Growing grievance and new norms make hostile activism and online harassment more common and, to some, seen as legitimate tactics.
Core principles: intent, context, speed
Before reacting, determine intent. Are actors seeking money, clout, political leverage, or provocation? Simon recommends assessing tactics and capabilities – single accounts, botnets, or coordinated supplier networks – to predict harm and inform response.
Speed is critical. The first hours determine whether an issue burns out or becomes embedded. But speed without coordination leads to mistakes. Most damaging outcomes come from the response, not the original post. If you treat reputation defense like a light switch you toggle once a problem happens, you will fail. Instead, build readiness ahead of time.
Simon coined the term strategic patience: monitor, map, scenario-play, then act in a measured, multidisciplinary way.
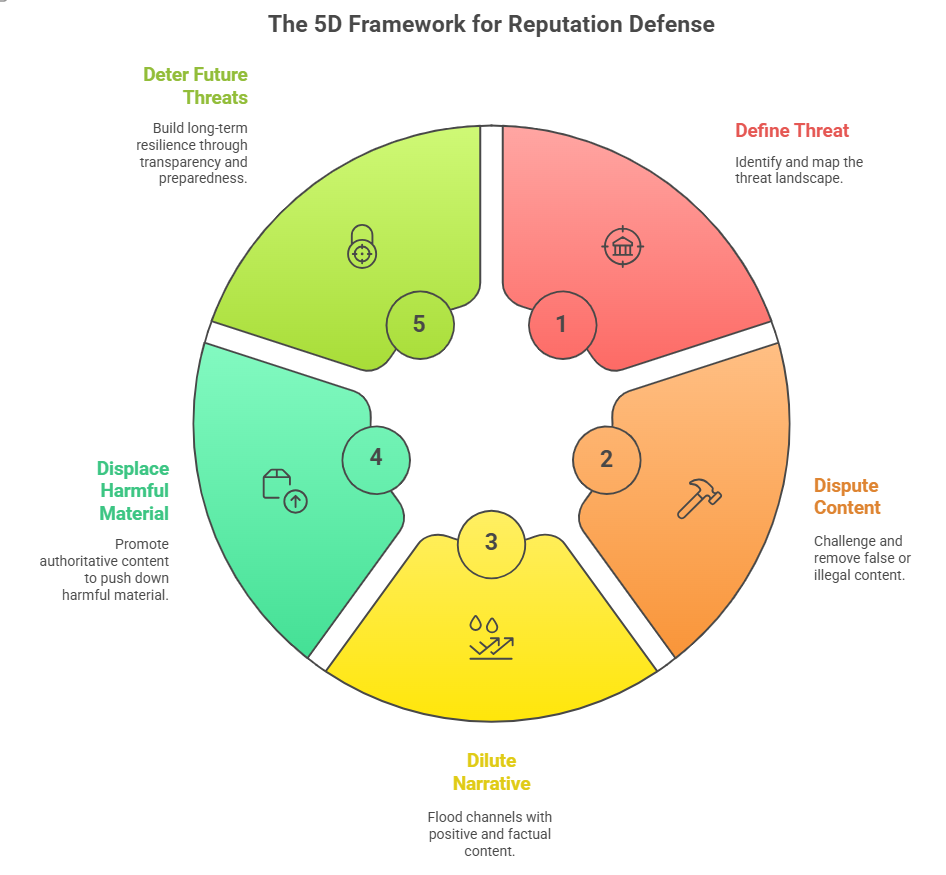
The 5D framework for rapid reputation defense
Use a coordinated, multidisciplinary approach. The five Ds give a practical workflow:
- Define — Map the threat: who started it, platforms, amplification nodes, geographic spread, and likely trajectories.
- Dispute — Challenge and remove false or illegal content via legal tools, platform escalation, and takedowns.
- Dilute — Flood relevant channels with factual, positive content and credible voices to lower the false narrative’s influence.
- Displace — Promote authoritative content to push harmful material down in search and feeds.
- Deter — Build long-term resilience through consistent transparency, policies, and preparedness exercises.
Trust Ops: who should be involved?
Rapid response is never just communications. Legal, security, intelligence, operations, and senior leadership must be coordinated. Consider a cross-functional council, trust ops, to ensure decisions are fast and aligned. But structure matters less than capability: you need monitoring, legal levers, comms agility, and external advice on call 24/7.
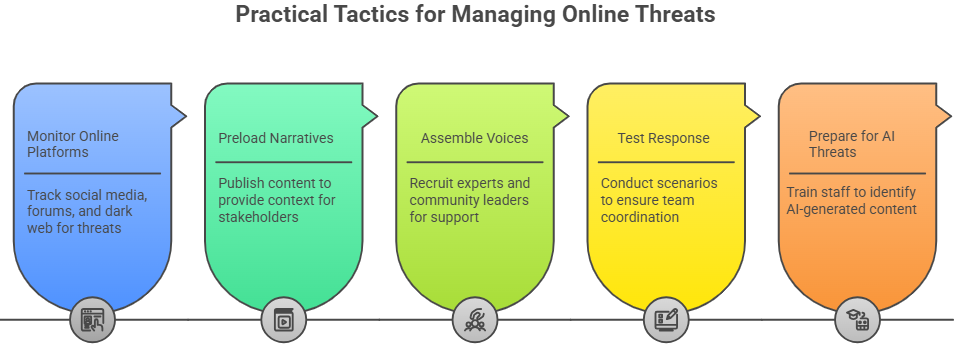
Practical tactics you can start using today
- Monitor broadly and in real time: social platforms, forums, fringe sites, and the dark web. You won’t be surprised by a sudden spike if you have good monitoring. measure spread, sentiment shifts, and whether additional action is needed.
- Preload narratives: publish defensible content and proof points now so your stakeholders have context when a false claim appears.
- Assemble your voices: recruit credible third parties – experts, customers, community leaders and influencers. Remember the importance of “Susans and Bobs” – experts and everyday trusted voices.
- Test your response: run scenarios and tabletop exercises so legal, comms, and security teams move together during the first hours. Assemble legal triage: evaluate takedowns, jurisdictional nuances, and enforceable remedies.
- Prepare for AI-driven threats: verify processes for voice and video authentication, and train staff to spot cloned audio, deepfakes, and synthetic text.
Short, direct advice
- Don’t stay silent. As Pavel advised, “If you leave the void there, somebody’s going to fill it.”
- Get ahead of it. When it comes to your public-facing narrative, as Simon advised, “If you’re not front-footed in what is now a deeply adversarial information environment, you are behind.”
- Be proactive. Build monitoring, response playbooks, and a cross-functional team now, not after a crisis.
Final thoughts
Disinformation targeting individuals is not a rare fringe issue anymore. It requires a strategic, proactive, and multidisciplinary response. As a rule of thumb: monitor widely, plan collaboratively, move deliberately, and always aim to control the narrative before it controls you.
This is a concise action plan for executives and their teams: monitor widely and in real time, map intent and spread, collaborate by assembling a multidisciplinary trust council, apply the 5Ds framework (Define, Dispute, Dilute, Displace, Deter), and build resilience by proactively owning your narrative. As Pavel put it, “one single tweet… can just literally rewrite the whole narrative about who they are.”
If you’re looking for more practical tools on defending you and your organization online and learn all about rapid response, visit Cyabra’s playbooks and guides.
Test yourself: Can you protect your reputation during an attack?
Don’t react impulsively. Assess intent and credibility first – determine who’s spreading it, where, and why – before launching a coordinated response.
Acting without coordination. Speed without strategy can amplify the issue – always align legal, comms, and leadership before speaking out.
A 5D defense framework (Define, Dispute, Dilute, Displace, Deter), preapproved messaging, and trusted voices ready to amplify the truth.
Map the threat. Identify origin points, bot activity, and spread trajectory to predict impact and decide whether to dispute, dilute, or escalate.
Use strategic patience – acknowledge the issue, share verified facts, and redirect focus with transparent, credible content. Never leave an information void.


