The last thing anyone wants is to stumble upon their own personal information posted online. This sentiment is even stronger for individuals who are public figures, journalists, CEOs, politicians, or celebrities.
Data leakage isn’t a new phenomenon. You might remember the huge cyber-attack on Sony Pictures in 2014, in which hackers stole employees’ social security numbers, medical records, salary information, and mail correspondences. The damage was so severe that even the FBI and former President Obama felt compelled to respond to the incident.
In each case of data leakage, the information that was leaked or stolen was private and highly sensitive to the individual and their respective organization. Could the leakage have been identified and prevented before significant harm ensued?
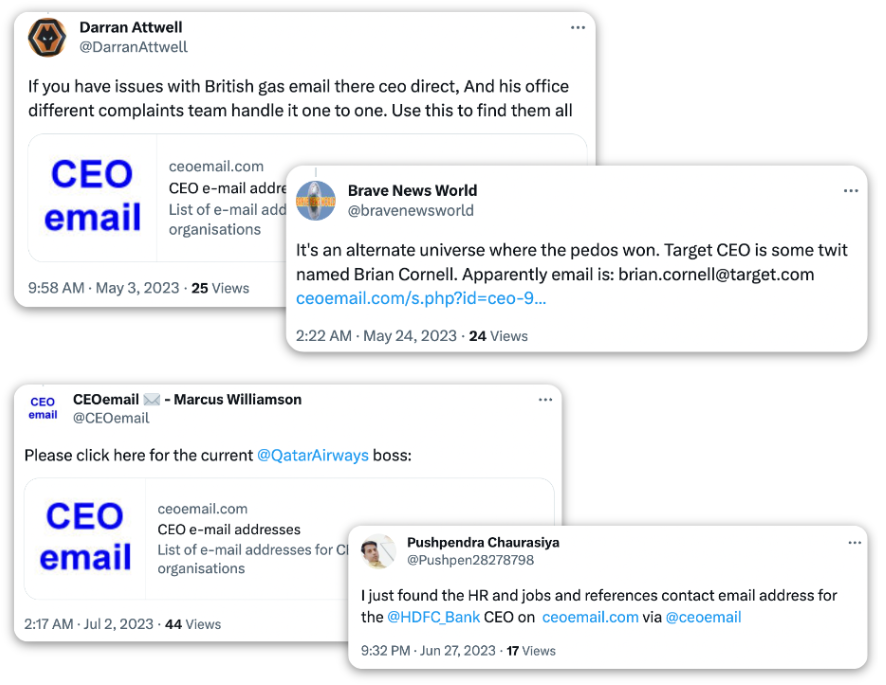
Let’s jump to the present: Cyabra detected 159 Twitter and Facebook profiles sharing private emails and phone numbers of CEOs and encouraging people to spam and harass them.
The CEOs whose contact details were exposed were the heads of huge corporates like HDFC and ICIC Banks, JPMorgan, Ticketmaster, McDonald’s, Target, Qatar Airways, British Gas company, and Morrisons, as well as many others.
If Your Contact Details Are Public, They Will Be Abused
Stolen data is always a matter of great concern for public figures and companies. It represents an opportunity for hackers and has the potential to cause great reputational damage.
The greater the size of a corporation, the greater the public interest in its leadership. Protecting the Personally Identifiable Information (PII) of CEOs, board members, and other important people at the top is crucial. This isn’t just a matter of executive protection, i.e. keeping their addresses confidential. Sometimes, a CEO’s email or phone number is everything a rising protest or a frustrated client base wishes for: the ability to utilize the power of the masses to flood, harass and eventually neutralize the companies’ leadership and force them to address the nuisance.
This form of harassment is so common that companies often choose to just replace the exposed email or phone number with a new one instead of tracking down the source, not realizing they are dealing with the symptoms and not with the problem.
Leaked Data: a Guide to Keeping Your Cool
There are two main differences between the 2014 Sony case and the new data leaks that Cyabra has uncovered: The first is the present-day prevailing use of social media platforms to weaponize this leaked information and spread it easily. The second difference is that we now have the capabilities to detect leaked data, track it back to its source, and take it down.
The harmful site featuring CEOs contact details was indeed eventually taken down, but Cyabra’s research uncovered that it has been active for months, causing enormous damage as it forced companies to deal with threats and harassment.
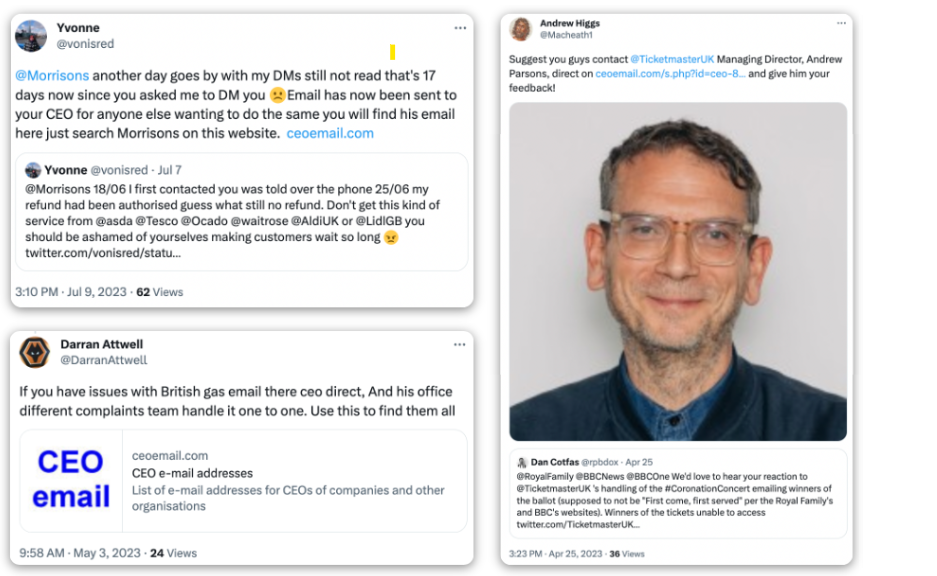
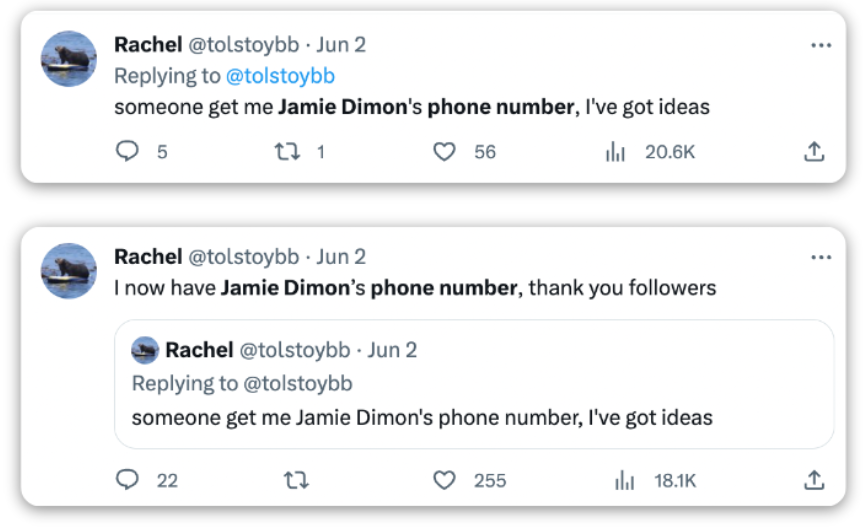
However, as mentioned above, the site was the symptom, not the problem. The use of social media platforms breaks new records every year, making it increasingly easy for users with even a moderate number of followers to uncover any information they desire. Check out the following posts: the profile, with 17,000 followers on Twitter, asked for the phone number of Jamie Dimon, CEO of JPMorgan. The request reached an exposure of 20,000 views, and accomplished its goal effortlessly in just a few hours. While this profile was not looking to publicly post the CEO’s phone number, the very ease of receiving this information should give pause to any Corporate Security team looking to protect their executives and management.
In conclusion, understanding the risks of online data leakage and protecting your company and people against the dangers has become crucial. If you’d like to learn more about the methods of detecting the threats and taking them down, contact Cyabra, and start proactively tracking threats in the online sphere.