Brand reputation can be destroyed in hours through coordinated social media attacks. Coordinated Inauthentic Behavior (CIB) on Facebook rapidly amplifies negative messaging and misinformation, damaging brand credibility before traditional systems detect the threat. According to Meta’s Transparency Center, significant gaps in platform-level detection require organizations to develop independent protection measures. This guide equips PR professionals with frameworks to identify CIB, implement detection systems, and execute strategic responses.
Understanding the Threat Landscape
Defining Coordinated Inauthentic Behavior (CIB)
The Meta Transparency Center defines CIB as “sophisticated forms of inauthentic behavior where inauthentic accounts are central to the operation and operators use adversarial methods to evade detection.” These campaigns create illusions of organic opinion while representing orchestrated attacks.
Key differences from legitimate criticism:
- Networks of accounts working together rather than individual users
- Deceptive tactics hiding true messaging sources
- Artificial amplification creating appearance of widespread sentiment
- Unusual timing and coordination patterns
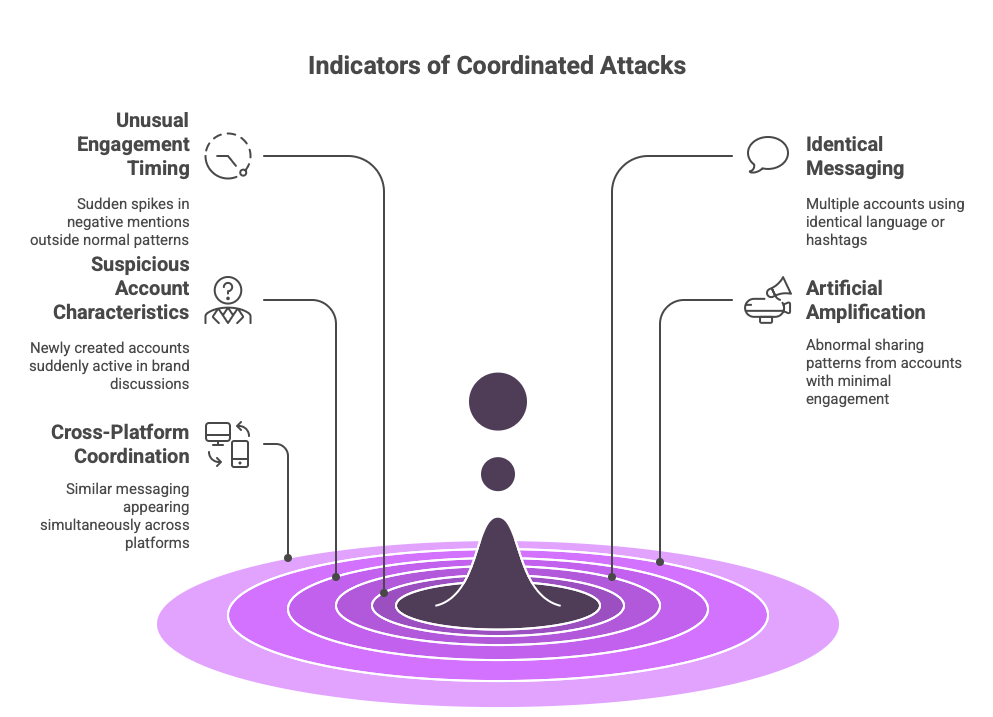
Key Indicators of Coordinated Attacks
- Unusual Engagement Timing: Sudden spikes in negative mentions outside normal patterns, especially during off-hours.
- Identical Messaging: Multiple accounts using identical language or hashtags within a compressed timeframe.
- Suspicious Account Characteristics: Newly created accounts with limited history suddenly active in brand discussions.
- Artificial Amplification: Abnormal sharing patterns from accounts with minimal previous brand engagement.
- Cross-Platform Coordination: Similar messaging appearing simultaneously across multiple platforms.
Building Your Early Warning System
Implementing Real-Time Monitoring Solutions
Your monitoring tools should deliver real-time alerts that catch the earliest signs of potential threats, such as:
- Sudden spikes in negative sentiment
- High-volume identical messaging
- Unusual engagement from new accounts
- Crisis keywords relevant to your organization
Establishing Baseline Metrics
- Volume Baselines: Document typical mention patterns including average volumes and standard deviations.
- Engagement Pattern Analysis: Map normal characteristics like typical account demographics and sentiment distribution.
From Detection to Action
Preparedness starts before a crisis: having a dedicated team on standby ensures you’re ready to act when negativity starts to build.
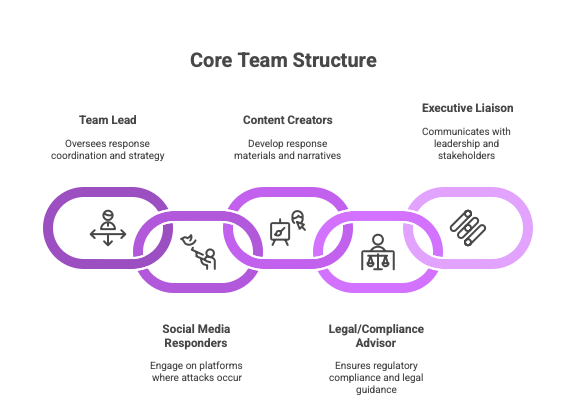
Core Team Structure:
- Team Lead: Oversees response coordination
- Social Media Responders: Engage on platforms where attacks occur
- Content Creators: Develop response materials
- Legal/Compliance Advisor: Ensures regulatory compliance
- Executive Liaison: Communicates with leadership
Advanced Detection Methods
Separating the good, bad, and fake involves a more advanced but achievable approach
- Sentiment Analysis Beyond Keywords: Consider the context and nuance, not just keywords.
- Fake Account Detection: Identify unusual account activity patterns or clusters of accounts operating in coordination.
- Language Pattern Analysis: Spotting message similarities indicate centralized creation.
Specialized Platforms for Campaign Detection
Cyabra Platform Capabilities:
- Network Analysis: Maps connections between accounts in coordinated networks
- Behavioral Pattern Identification: Analyzes posting patterns to distinguish authentic from inauthentic behaviors
- Content Authenticity Verification: Identifies manipulated media and misleading content
- Real-Time Monitoring: Provides continuous surveillance for emerging threats
Organizations using Cyabra report
- Identification of coordinated networks with over 90% accuracy
- Detection of suspicious activity within minutes
- Reduction of false positives by up to 83%
Hybrid Human-AI Approaches
The most effective systems combine AI analysis with human expertise:
- Human-in-the-Loop Systems: Implement workflows where AI flags suspicious patterns for human review.
- Analyst Augmentation Tools: Provide visualization interfaces enhancing pattern recognition.
- Continuous Learning Frameworks: Establish feedback loops where analyst insights improve AI detection.
Building Resilience Through Transparency
- Transparency Infrastructure: Create dedicated portals providing stakeholders with accurate information during crises.
- Stakeholder Education: Develop content helping stakeholders recognize coordinated inauthentic behavior.
The most resilient organizations combine
- Technological solutions providing early detection
- Human expertise contextualizing threats
- Proactive strategies building reputation reserves
- Transparent communication maintaining stakeholder trust
- Continuous learning improving capabilities
Conclusion
The landscape of coordinated inauthentic behavior continues evolving with increasingly sophisticated methods. For PR professionals protecting brand reputation, comprehensive detection and response frameworks are essential components of modern reputation management.
By implementing these strategies, organizations can transform from reactive crisis victims to proactive reputation defenders, maintaining narrative control even during coordinated attacks.
_____________
Cyabra’s platform delivers advanced AI-powered detection, multi-signal monitoring, and real-time alerting. Cyabra specializes in detecting inauthentic behavior using AI to identify fake accounts, coordination patterns, and misinformation campaigns, transforming crisis management from reactive damage control to proactive reputation defense. Contact us to learn more.